Security Journey
Security Posture Management as a Service
Role:
Senior Manager → Director of Concierge Security (Promoted during project)
Timeline:
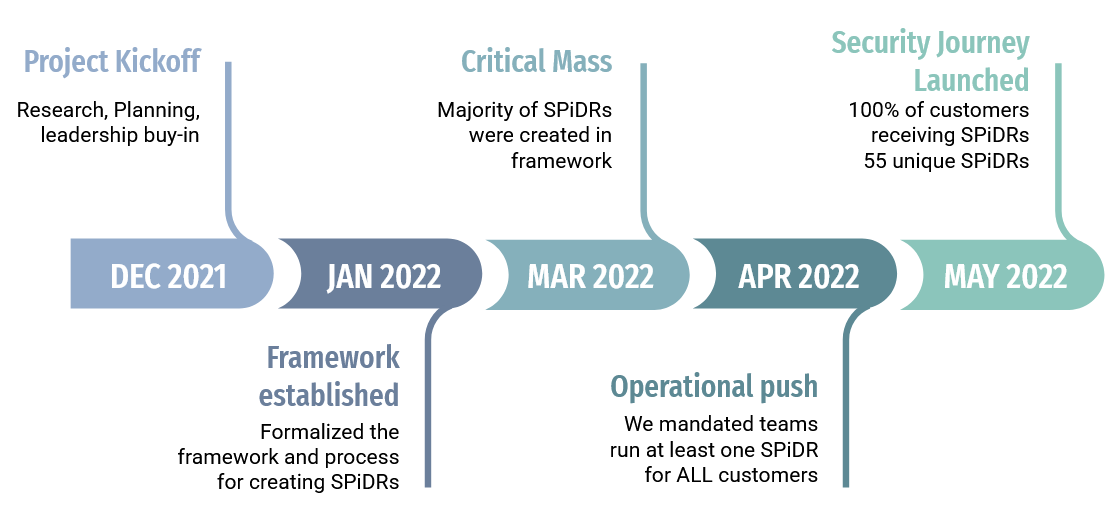
6 Months (Dec 2021 - May 2022)
Team:
1 Security Ops Manager, 3-4 Security Technical Leads
The Challenge
Arctic Wolf's Concierge Security team had scaled from 15 to 150 engineers over 3.5 years, but growth exposed a critical problem: customers received wildly inconsistent security guidance depending on which team they were assigned to.
We had "good teams" with deep expertise across multiple domains, but most teams were specialists in one or two areas. A customer assigned to a firewall expert would get excellent network security guidance but surface level endpoint hardening recommendations. One customer suffered an entirely preventable Active Directory breach because their assigned engineer hadn't looked into their AD in months.
Engineers conducted ad-hoc security reviews based on tribal knowledge with no standardized framework, investigation playbooks, or consistent deliverables. Service quality was entirely dependent on team assignment. That wasn't sustainable for hundreds of engineers with plans to double again.
The Constraint:
Concierge Security is an operations team that had no development or product support during this time. I needed to standardize and scale expertise across hundreds of engineers without formal product infrastructure.
My Approach
Became the product manager we didn't have
I took this on as a product initiative despite being a Senior Manager in operations. With their support (but no additional budget or headcount), I ran it like a proper product build with stakeholder check-ins, clear success criteria, and a six-month timeline. This became 40% of my time.
Extracted repeatable patterns from top performers
I identified our "churn-save teams," shadowed them, and documented their investigation techniques. They were doing comprehensive deep-dives across multiple security domains and helping customers prioritize mitigations based on business needs rather than just listing technical gaps. That became the template for the framework.
Built a framework that scaled expertise through SME partnerships
I created the SPiDR methodology with clear structure: investigation resources, competency requirements, NIST alignment, and deliverable templates. Then I partnered with three technical leads who were domain experts. They drafted content for their respective domains while I ran a centralized review process to ensure quality and consistency. We also designed the supporting workflows: how engineers would track delivery, how customers would receive varied content based on maturity, and how we'd measure adoption.
Shipped manually without waiting for product infrastructure
Without product infrastructure, we managed everything through Confluence docs and spreadsheets. We built procedures around keeping track of the work performed using templated spreadsheets and tracked the deliverables via ticket tags.
The Solution
Security Journey formalized Arctic Wolf's proactive security practice through a library of 55 security posture modules tailored to different customer maturity levels.
Each SPiDR guided engineers through structured security assessments, provided customer-ready deliverables, and mapped findings to NIST frameworks, and provided mitigations for identified risks and gaps.
Engineers could now deliver comprehensive security reviews across all domains, even outside their core expertise.
We packaged SPiDRs into "Security Focuses," collections targeting specific customer goals and maturity levels. This ensured customers received varied but relevant content across all domains of interest rather than repetitive reviews in a single area.
Without product infrastructure, we managed delivery through Confluence docs and spreadsheets. It was brutal and manual, but it worked.
What SPiDRs actually find:
SPiDRs (Security Posture In-Depth Reviews) are investigation playbooks that systematically identify security gaps across domains. Each SPiDR guides engineers through structured assessments, looking for specific behaviours and signals that may indicate gaps such as the following:
Unpatched systems: Critical vulnerabilities in servers, endpoints, and infrastructure left exposed to known exploits
Security control failures: Monitoring agents offline, defensive tools disabled, logging gaps that create blind spots
Misconfigurations: Overly permissive firewall rules, exposed management interfaces, weak authentication policies
Encryption and data protection gaps: Unencrypted traffic floating across the network, exposed credentials
Unauthorized access and software: Shadow IT applications, excessive privileges, unapproved tools
Cloud security risks: Publicly accessible storage buckets, misconfigured IAM policies, unmonitored cloud workloads
Identity and authentication weaknesses: Password policy gaps, missing MFA enforcement, stale accounts with active access
The framework ensured every engineer - regardless of expertise - could identify these gaps consistently as we had boiled the problem space down to identifying the risk’s indicators and mitigations.
Key Capabilities:
Maturity-based content: Different SPiDRs for different customer archetypes. Enterprise vs. SMB, regulated vs. unregulated, each got appropriate depth and complexity
Expertise democratization: Engineers could deliver high-quality reviews outside their core expertise by following SPiDR guidance, eliminating the "expertise lottery" of team assignment
Security Focuses: Collections of SPiDRs targeting specific customer goals ("Harden my perimeter," "Revamp Active Directory," "I need a bit of everything")
Standardized deliverables: Each SPiDR produced consistent outputs (live presentation, PDF report, raw data exports, actionable mitigation tasks)
NIST framework mapping: All findings aligned to NIST CSF for compliance and strategic planning
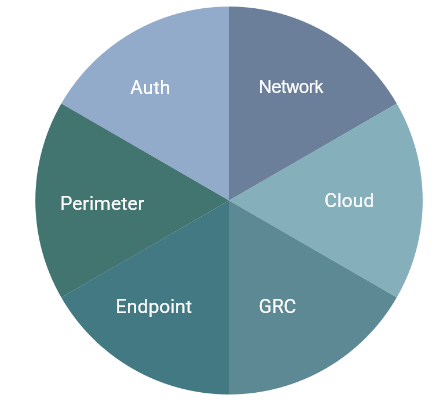
Security Domains SPiDRs focus on
How It's Evolved
Three years later, SPiDRs remain central to Arctic Wolf's value proposition but are now deeply productized with self-service customer portal access, automation, and an expanded catalog of 200+ SPiDRs. Security Journey became the one of the main service models that Command Center operationalized.
The Impact
Operational transformation:
Security Journey transformed Arctic Wolf's ad-hoc practice into the company's primary service differentiator within six months.
55 SPiDRs created across seven security domains in six months (built to 200+ over three years)
Customer escalations dropped significantly. Reassignments due to poor service quality became rare
Onboarding accelerated. New engineers could deliver comprehensive reviews using standardized playbooks instead of months of tribal knowledge transfer
Preventable incidents eliminated. Customers who previously slipped through gaps now received proactive identification across all domains
The biggest impact: we raised the baseline. The service from even the newest team became significantly better.
Business impact:
Sales leadership highlighted Security Journey and Concierge as the differentiator in competitive deals. "We only win against <main competitor> because of the Concierge offering" became the standard sales narrative. Security Journey became the primary deliverable of a 200+ person team supporting the company's entire customer base.
Career impact:
I was informed of my promotion to Director of Concierge Security in March 2022. Four months later, when Director of Product opened, I was the obvious choice. I'd already proven I could build products, drive business outcomes, and think strategically without formal product resources.
Key Learnings
Ship manually, automate later - prove value before asking for resources
We didn't wait for development funding or product infrastructure. We built with Confluence docs, spreadsheets, and manual workflows. That scrappy execution proved business value (sales differentiator, customer satisfaction, reduced escalations) which unlocked investment. SPiDRs are now fully productized in Command Center with self-service portal access, automated investigations, and integrated task management.
Frameworks accelerate execution when constraints are tight
The SPiDR methodology let three technical leads produce 55 high-quality playbooks in six months while juggling other responsibilities. When you can't add headcount, invest in the system that multiplies existing talent.